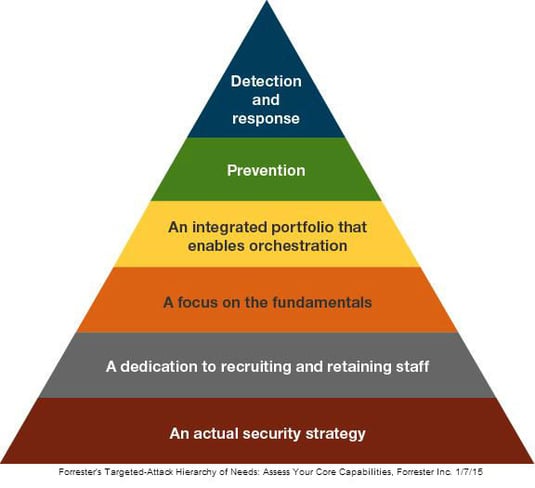
In the first part of cybersecurity planning, we discussed the top-level alignment of your security strategy with “The 3 R’s”:
- What gets you Rich?
- What can Ruin your business?
- What is Required by regulators or customers?
The 3 R’s are largely business drivers, not technology or security drivers. In part 2 of this series, we go into more depth and bring cybersecurity experience and expertise into the planning exercise to understand detailed requirements for cybersecurity.
Building on the 3 R’s defined in part 1, some activities you’ll perform next are:
1. A needs analysis of your revenue-facing systems and processes
Assuming your systems are performing well for the business, you will be focused on needs related to: Confidentiality, Integrity and Availability of data and systems.
When choosing what systems to investigate, look for systems that support the primary mission of the business. Likely candidates are: Point-of-Sale, e-commerce, sales, finance and communication systems. When understanding the needs of these systems and processes, ask the business owners and users “what happens if you can’t use the system?” You’ll be amazed at what you discover.
2. A compliance analysis to understand what regulations apply to your business
Think you’re not regulated? While you may not be directly regulated, your customers today and tomorrow may be. Many of your customers’ requirements flow through to you as a vendor.
Understanding compliance requirements includes both what prospective controls must be in place as well as the processes and procedures for incident response and business continuity. As you go through this analysis, understanding the complex, overlapping requirements for regulations generally requires regulatory experience and skills. If you don’t have the necessary skills and experience in-house, find a reputable vendor or consultant to help.
3. A threat analysis to understand what factors can do harm to your business
Threats can be human or non-human, malicious or non-malicious. Threats can originate from natural disasters, software, political activism, external vulnerabilities or internal mistakes.
Hackers get the press, but most incidents are self-inflicted. Understanding how your systems can be taken down and how data can be breached is an important step in creating a real strategy. Without a threat model and some investigation to test the model, you don’t know what you don’t know. I can’t stress enough how important it is to understand what threats you face BEFORE you begin your risk assessment and strategic plan.
Third-Party Analysis Leads to a Roadmap for Security
Step one can and should be performed by in-house employees. Defining the 3 R’s should be normal business practice for everyone. When it comes time to perform the objective analysis of your business, an external 3rd party can be very useful. Uncovering areas where employees may be afraid to look or unwilling to report bad news is the job of 3rd party consultants. Giving objective information back to the business allows companies to fix what’s wrong and focus on building team processes for the future.
Once an organization has documented the 3 R’s and quantified the needs, compliance requirements and threats to the business, you can move towards the risk assessment that will lead to a strategic plan and roadmap for security.